DoubleDrive: leveraging cloud services as ransomware agents
In a world where ransomware attacks are growing increasingly sophisticated, Or Yair presented an innovative and concerning method for executing ransomware attacks at CONFidence 2024. Named “DoubleDrive,” this attack exploits the synchronization mechanisms of popular cloud storage services – OneDrive and Google Drive – to bypass traditional security measures. Read our summary and watch the full lecture on YouTube.
What is DoubleDrive?
DoubleDrive represents a novel approach to ransomware that operates entirely through legitimate cloud storage agents. It transforms cloud services into unwitting accomplices by synchronizing, encrypting, and altering files without requiring a malicious executable to be present on the victim’s machine. This method makes detection and prevention extremely challenging.
Key features of DoubleDrive
- Undetectable by design: DoubleDrive leverages legitimate processes and APIs, bypassing traditional ransomware detection methods.
- Cloud agent exploitation: It utilizes OneDrive and Google Drive’s built-in synchronization features to perform file encryption and deletion.
- Token hijacking: By stealing access tokens stored locally, attackers gain control over cloud accounts without raising alarms.
- No malicious executable: DoubleDrive doesn’t leave a malicious executable on the target system, making static signature detection ineffective.
How does DoubleDrive work?
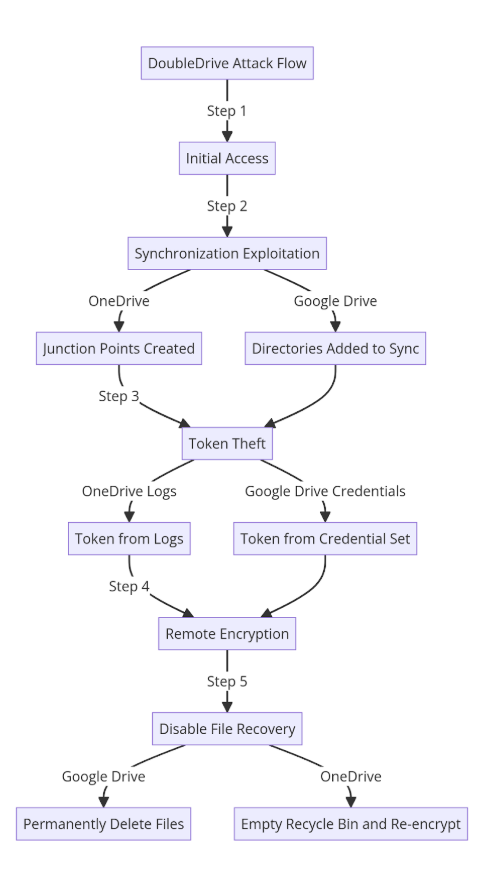
The attacker gains access to the victim’s computer, often through traditional methods like phishing or exploiting vulnerabilities. In OneDrive, attackers create junction points in the OneDrive sync folder, directing the agent to synchronize target directories. In Google Drive, they programmatically add local directories to the sync database.
Attackers extract cloud access tokens stored locally: in the current user’s credential set (Google Drive) or log files, accessible with user permissions (OneDrive). Using stolen tokens, attackers encrypt files stored in the cloud. The changes propagate back to the victim’s local directories via synchronization, effectively encrypting local files.
Attackers exploit or disable recovery mechanisms. APIs are used to permanently delete files and erase version history on Google Drive or recycle bins are emptied, and files are re-encrypted to prevent restoration on OneDrive.
If you want to learn about other new attack methods, join the CONFidence conference in 2025.
Why is this attack effective?
Bypassing Endpoint Detection and Response (EDR)
Traditional EDR systems trust OneDrive and Google Drive processes by default. This trust allows DoubleDrive to encrypt files without triggering alarms and avoid detection even when modifying decoy files used by EDRs.
Exploiting trust in cloud services
Cloud storage services are trusted both by users and security systems. DoubleDrive takes advantage of this trust to carry out its operations.
API Abuse
The attack uses legitimate APIs to synchronize directories, steal access tokens, and delete file histories, leaving no trace of the original files.
Implications for security
DoubleDrive highlights a major gap in current security practices:
- Default trust: Legitimate applications like OneDrive and Google Drive should not be trusted by default without strict monitoring.
- Token security: Access tokens must be stored securely and made inaccessible to non-administrative processes.
- Enhanced EDR capabilities: Security solutions need to account for attacks leveraging legitimate software and APIs.
Mitigation strategies
- Token protection: Implement stricter policies for token storage and access, ensuring they are encrypted and protected by multi-factor authentication.
- Cloud activity monitoring: Actively monitor unusual activity in cloud accounts, such as large-scale deletions or file modifications.
- Endpoint security enhancements: Develop detection mechanisms that focus on behavior rather than static signatures, specifically targeting API misuse.
- User education: Train users to recognize phishing attempts and avoid granting excessive permissions to unknown applications.
Conclusion
DoubleDrive serves as a wake-up call for both users and security professionals. As ransomware evolves to exploit legitimate services, traditional security measures must adapt. By implementing stricter controls over trusted applications and focusing on behavioral analysis, organizations can mitigate the risks posed by sophisticated attacks like DoubleDrive.